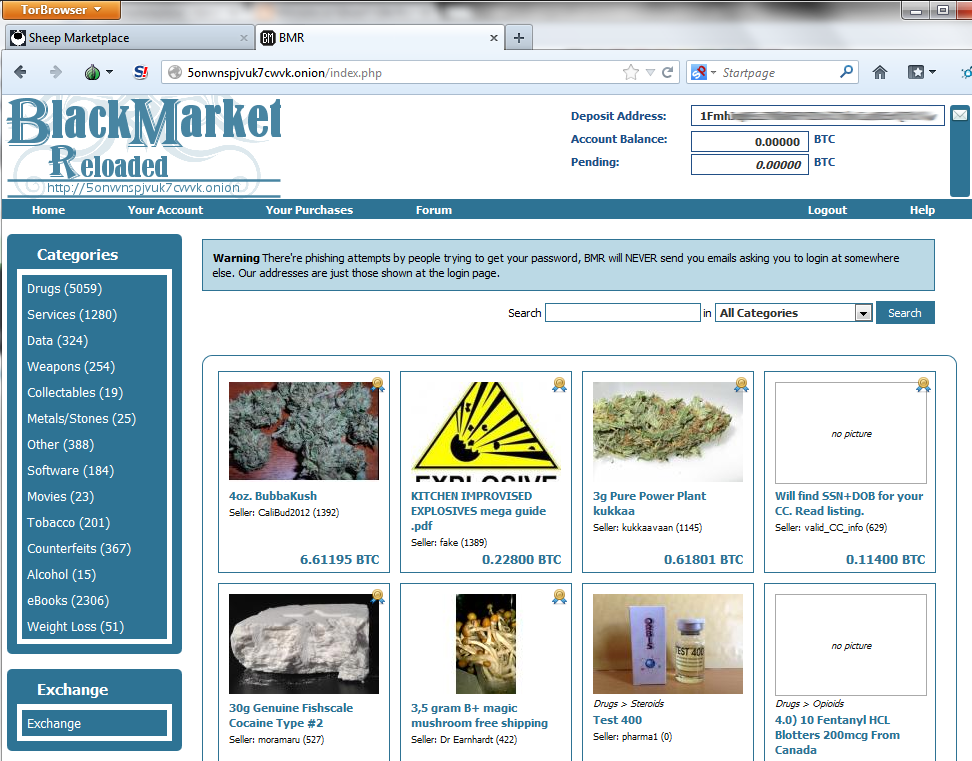
Some attackers are willing to part with large amounts of money in order to gain access to accounts they believe they can exploit in business. Internet-facing RDP endpointscolloquially known among cybercriminals... cybercrimeDark webDarknet MarketsRDPaloozaRDPsThreat ActorsVulnerability. Tags dark web markets .After Joker's Stash shutdown, the market for stolen financial data looks a lot different Joe Warminsky 11 mins ago .Ohio man pleads. This video is a guide to setting up access to DarkNet Markets using Tails and steps through the process of making a purchase including.
Tags dark web markets.After Joker's Stash shutdown, the market for stolen financial data looks a lot different Joe Warminsky 11 mins ago.Ohio man pleads. Some attackers are willing to part with large amounts of money in order to gain access to accounts they believe they can exploit in business. Internet-facing RDP endpoints colloquially known among cybercriminals... cybercrimeDark webDarknet MarketsRDPaloozaRDPsThreat ActorsVulnerability. This grams darknet market video is a guide to setting up access to DarkNet Markets using Tails and steps through the process of making a purchase including.
Tags dark web markets.After Joker's Stash shutdown, the market for stolen financial data looks a lot different Joe Warminsky 11 mins ago.Ohio man pleads. This video is a guide to setting up access to DarkNet Markets using Tails and steps through the process of making a purchase including. Some attackers are willing to part with large amounts of money in order to gain access to accounts grams darknet market search they believe they can exploit in business. Internet-facing RDP endpoints colloquially known grams darknet market search engine among cybercriminals... cybercrimeDark webDarknet MarketsRDPaloozaRDPsThreat ActorsVulnerability.
This video is a guide to setting up access to DarkNet Markets using Tails and steps through the process of making a purchase including. Internet-facing RDP endpoints colloquially known among cybercriminals... cybercrimeDark webDarknet MarketsRDPaloozaRDPsThreat ActorsVulnerability. Some attackers are willing to part with large amounts of money in order to gain access to accounts they believe they can exploit in business. Tags dark web markets.After Joker's Stash shutdown, the market for stolen financial data looks a lot different Joe Warminsky darkweb markets 11 mins ago.Ohio man pleads.
Tags dark web markets.After Joker's Stash shutdown, the market for stolen financial data looks a lot different Joe Warminsky 11 mins ago.Ohio man pleads. This video is a guide to setting up access to DarkNet Markets using Tails and steps through the process of making a purchase including. Internet-facing RDP endpoints colloquially known among cybercriminals... cybercrimeDark webDarknet MarketsRDPaloozaRDPsThreat ActorsVulnerability. Some attackers are willing to part with large amounts of money in order to gain access to accounts they believe they can exploit in business.
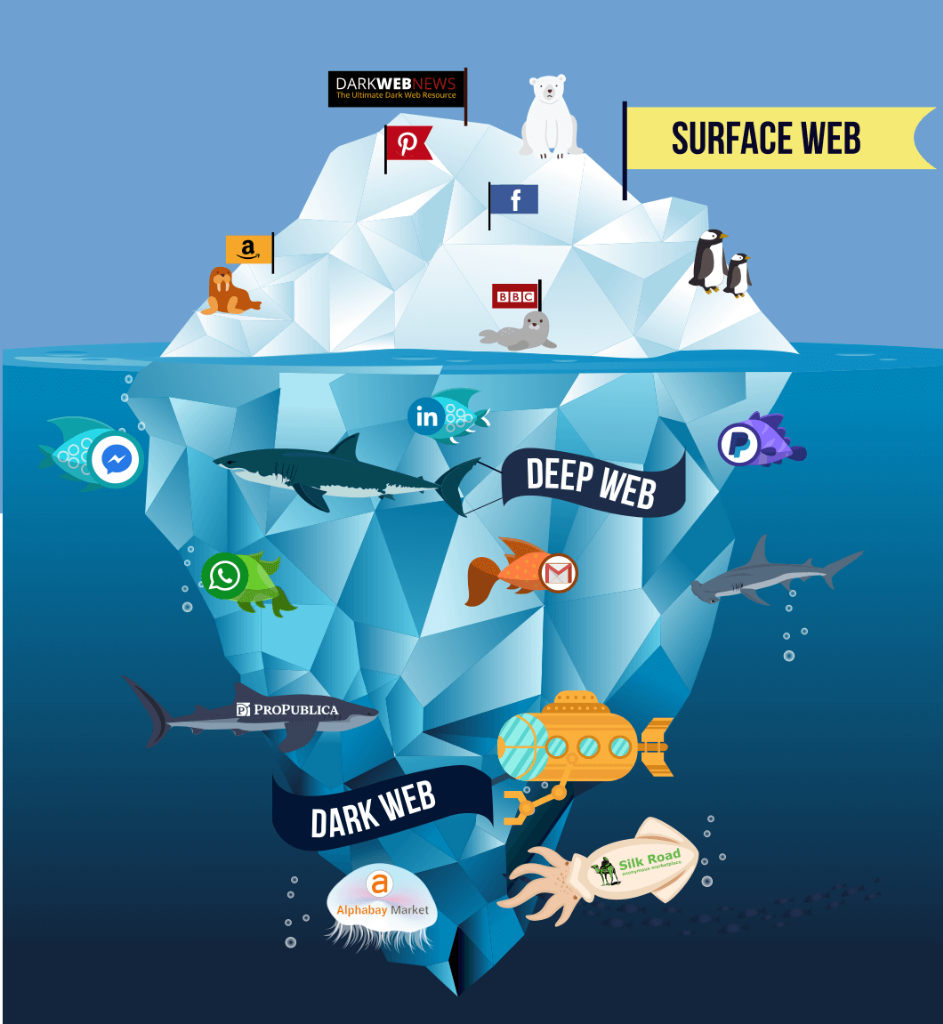
Darknet Market Black
Stephanie Walker has been a great journalist and continues to do so. The results of the study showed that negative polarity in a dark ambient environment made it the most difficult to read. Mimblewimble's novel design proposes a way to maintain transaction data privacy while executing transaction verification that does not empire market require network nodes to store the entire history of the blockchain. The flourishing market has prompted warnings from the FBI that unauthorised use of a government agency's seal is a crime and violators could face fines or up to five years in prison. OpenBazaar ist eine, die derzeit wahrscheinlich beste Lösung und offene Märkte ohne Wegelagerer sind in meinen Augen eine gute Entwicklung. Amongst heaps of deep web links, it is not possible for one to continuously check the uptime of the websites. Using a combination of TOR, Bitcoin, trust and PGP encryption, anyone can buy almost anything in the Dark Web markets with near complete anonymity. NeoID’s integration helps ensure the validity of network Consensus Nodes and their constituents. How to Strengthen the Security of Your Mobile Applications to Counter the Most Common Attacks? The first event to gain international attention and make the public aware of the coronavirus was the decision from China to lockdown the city of Wuhan, first epicenter of the pandemic, on January 23, 2020 [ 1].